Enterprise AI Security Toward AI Agent

AI security vulnerabilities are creating unprecedented risks. Every AI deployment without proper identity controls becomes a potential backdoor for cybercriminals.
The Game-Changing Solution to Reduce Kafka Traffic Costs
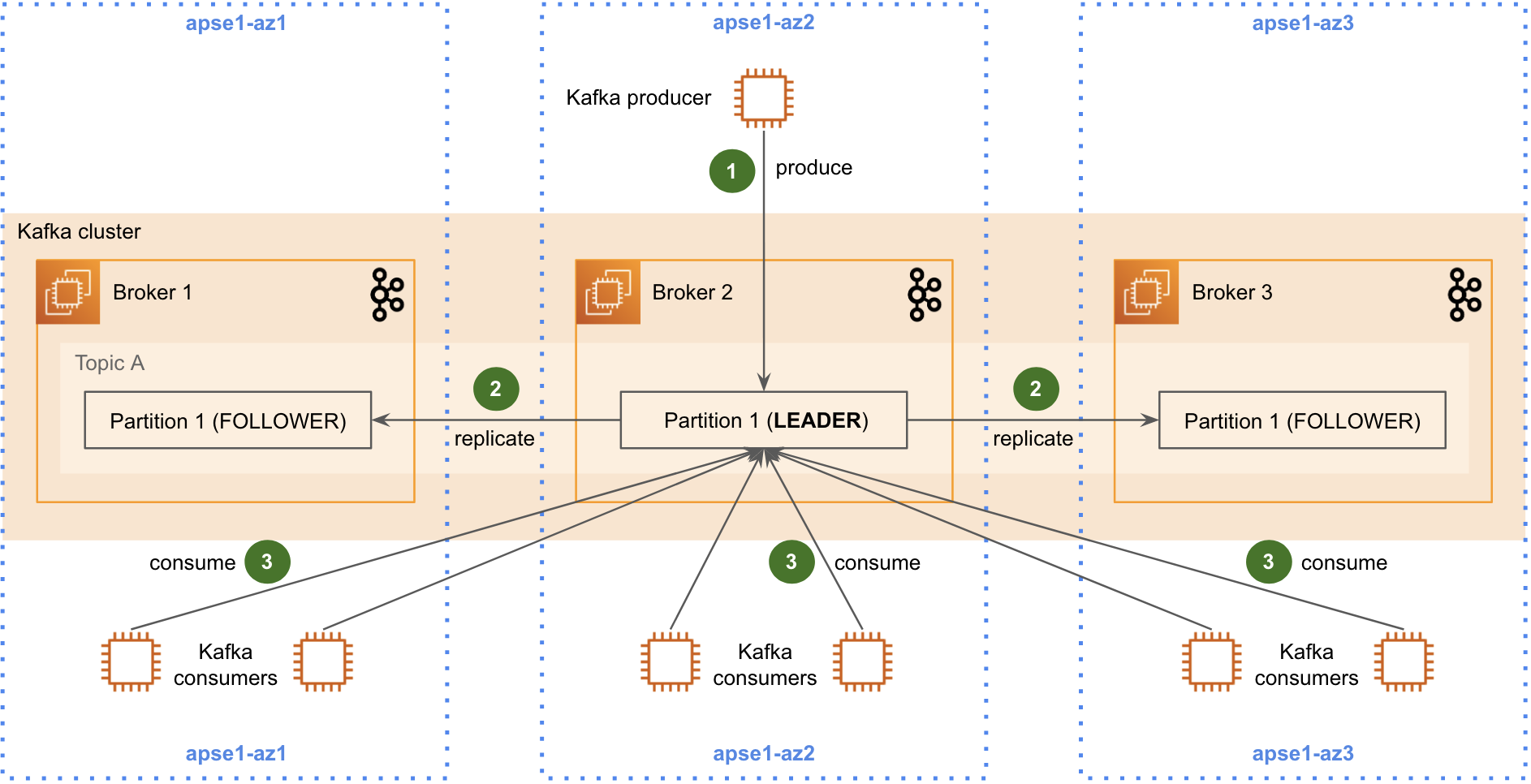
Learn how to reduce Kafka AWS cross-AZ traffic costs by 25% using closest replica fetching. Step-by-step guide with real implementation examples and cost savings analysis.
Securing Kubernetes Cluster Configuration
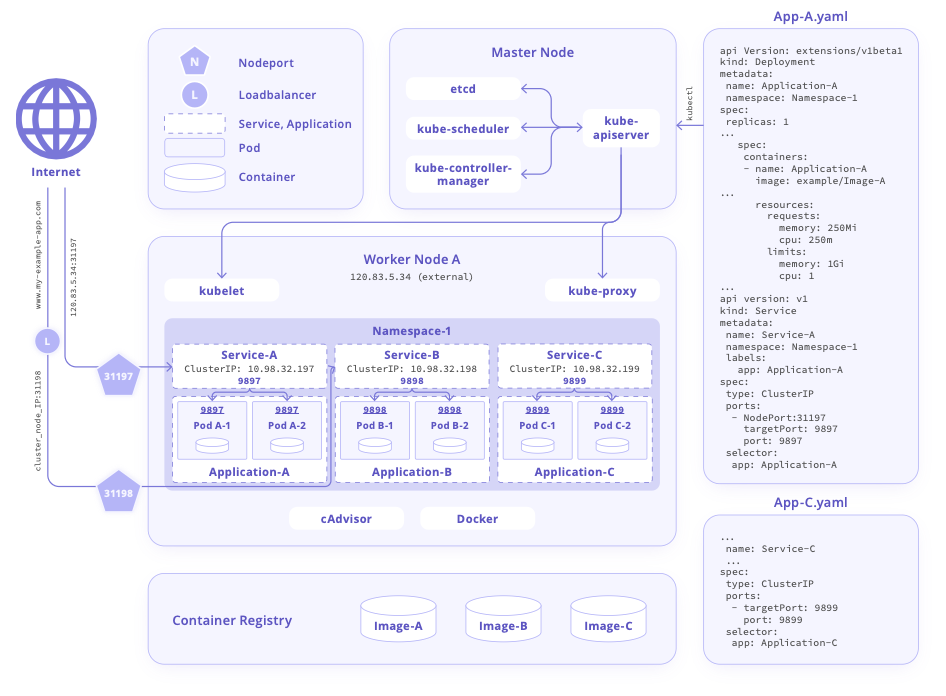
Learn comprehensive kubernetes cluster security configuration best practices, including master node hardening, worker node security, Infrastructure-as-Code practices, and secure configuration management for robust container orchestration.
AI-Powered Security With LLM Agents
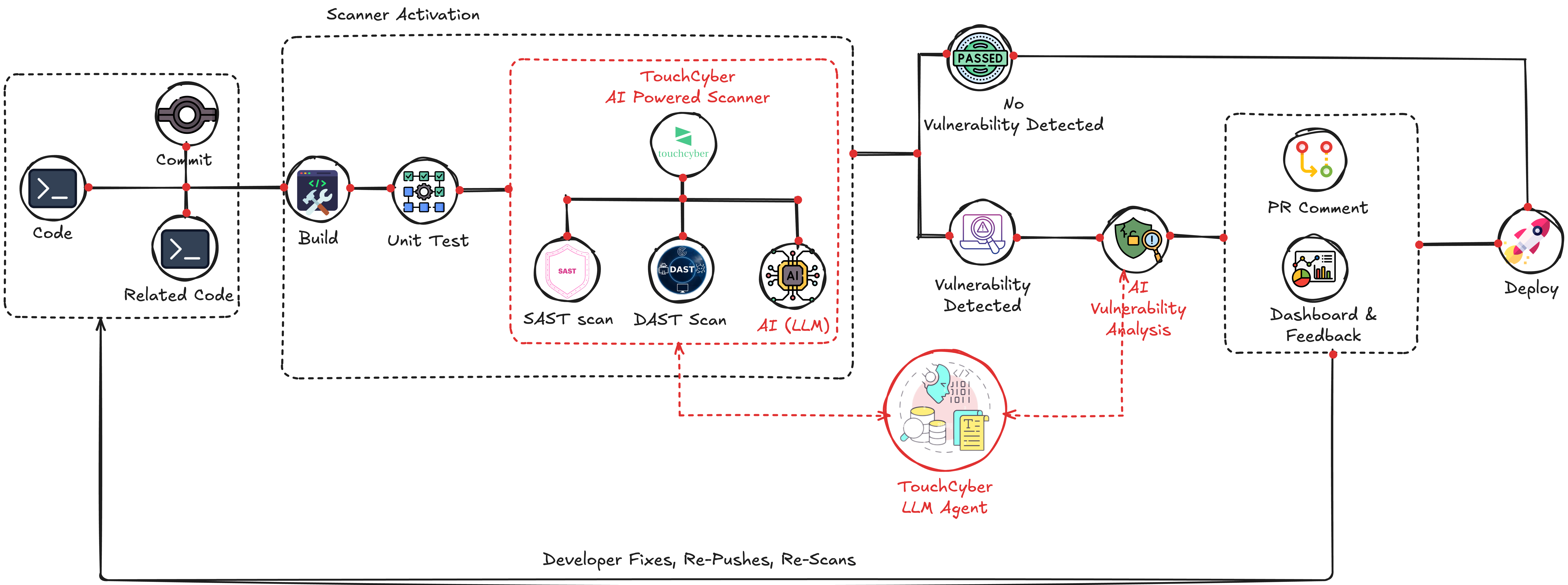
Discover how AI-powered security scanners and LLM agents are transforming blockchain security through automated vulnerability detection in CI/CD pipelines. Learn about TouchCyber’s innovative approach to blockchain security.
How to Find Private Keys on GitHub Using OSINT

Discover how to find private keys on GitHub using OSINT techniques. Learn advanced search queries, automation tools, and ethical bug bounty practices for security researchers.
OAuth Attack Surface Mapping Using URLScan Dorking
Learn how to perform effective OAuth attack surface mapping using URLScan dorking techniques to discover vulnerable authentication implementations and expand your bug bounty hunting success.
